
Tech Data Consulting, the leading pan-African* distributor for Cybersecurity, Datacentre, Cloud, Surveillance, and IoT Solutions, has become Master Distributor for Fortinet, a global leader in broad, integrated, and automated cybersecurity solutions.
Fortinet secures the largest enterprise, service provider, and government organizations around the world. Fortinet empowers its customers with intelligent, seamless protection across the expanding attack surface and the power to take on ever-increasing performance requirements of the borderless network—today and into the future.
Only the Fortinet Security Fabric architecture can deliver security without compromise to address the most critical security challenges, whether in networked, application, cloud, or mobile environments. Fortinet ranks number one in the most security appliances shipped worldwide and more than 500,000 customers trust Fortinet to protect their businesses.
Tech Data Consulting has extensive pre-sales and technical resources and offers its partners the skills and expertise they need to ensure their customers get the best possible experience with Fortinet.
*South Africa, Botswana, Namibia, Zambia, Angola, Zimbabwe, Malawi, Mozambique, Malawi, Lesotho, Swaziland, Madagascar, Mauritius, and Seychelles.

The Fortinet Security Fabric is the industry’s highest-performing cybersecurity platform, powered by FortiOS, with a rich open ecosystem. It spans the extended digital attack surface and cycle, enabling self-healing security and networking to protect devices, data, and applications.
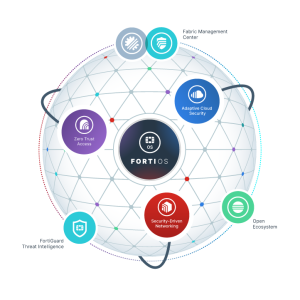
Fortinet’s Security-driven Networking strategy tightly integrates an organization’s network infrastructure and security architecture, enabling the network to scale and change without compromising security. This next generation approach is essential for effectively defending today’s highly dynamic environments – not only by providing consistent enforcement across today’s highly flexible perimeters, but by also weaving security deep into the network itself.
Adaptive Cloud Security
As cloud adoption accelerates, organizations are increasingly reliant on cloud-based services and infrastructures. Fortinet Adaptive Cloud Security Solutions provide the necessary visibility and control across cloud infrastructures, enabling secure applications and connectivity from data center to cloud.
Zero Trust Access
The growth of insecure or unknown devices attaching to the network, along with a host of breaches due to stolen credentials, has stretched trust beyond the breaking point. Fortinet Network Access solutions offer the necessary device security to see and control all devices and users across the entire network.
Endpoint Security
Combining behavior-based endpoint protection, detection, and response offers a modern approach to endpoint security. Fortinet uses multiple machine learning and deep learning technologies to power all three functions at each endpoint.
Operational Technology
As organizations adopt new digital technologies, industrial networks are intersecting with internet-connected corporate networks. This operational technology (OT) and information technology (IT) convergence expands the number of internet-enabled, agentless IoT devices requiring security to reduce risk. Fortinet’s Security Fabric secures the entire OT/IT attack surface.
 Fortinet Secure SD-WAN powered by Security-driven Networking and purpose-built processors enables infrastructure and networking teams to deliver improved user experience, instant ROI, and simplified operations. An integral part of the Fortinet Security Fabric, FortiGate NGFWs utilize purpose-built security processors and threat intelligence security services from FortiGuard labs to deliver top-rated protection and high performance including encrypted traffic visibility.
Fortinet Secure SD-WAN powered by Security-driven Networking and purpose-built processors enables infrastructure and networking teams to deliver improved user experience, instant ROI, and simplified operations. An integral part of the Fortinet Security Fabric, FortiGate NGFWs utilize purpose-built security processors and threat intelligence security services from FortiGuard labs to deliver top-rated protection and high performance including encrypted traffic visibility.

Adaptive Cloud
As cloud adoption accelerates, organizations are increasingly reliant on secure cloud solutions and infrastructures. Yet, organizations often end up with a heterogeneous set of technologies in use, with disparate cloud security controls in various cloud environments. Fortinet Adaptive Cloud Security Solutions provide the necessary visibility and control across cloud cybersecurity infrastructures, enabling secure applications and connectivity from data center to cloud.

Zero Trust Access
Zero Trust Access from Fortinet enables network operators to know and control everyone and everything on the network, including controlling managed devices when off-network.
Network Access Control (NAC)
Network access control, or NAC, is a zero trust access solution that provides users with enhanced visibility into the Internet of Things (IoT) devices on their corporate networks.
Teleworker
Fortinet solutions securely support a remote workforce which is an essential component of any organization’s business continuity and disaster recovery plan.

Extended Detection and Response (XDR)

FortiXDR adds fully-automated extended detection and response (XDR) across the Fortinet Security Fabric to improve an organization’s security posture and operational efficiency.
Endpoint Protection, Detection, and Response (EDR)

FortiEDR delivers real-time automated endpoint protection both pre- and post-infection, detecting and defusing threats in real-time to stop breaches, while automating the response and remediation process.

Operational Technology
Operational technology (OT) is the use of hardware and software to monitor and control physical processes, devices, and infrastruture. Operational technology systems are found across a large range of asset-intensive sectors, performing a wide variety of tasks ranging from monitoring critical infrastrucure (CI) to controlling robots on a manufacturing floor.
How to get Started
For more information on how to get started or general inquiries:
